Even the best enterprise cybersecurity workflows suffer from scalability issues.
An enterprise tech stack can contain anywhere from 50 to 100 separate security technologies, each with its own set of workflows and requisite skill sets. Expanding this tech stack to accommodate growth is a steep challenge that many enterprise leaders are not prepared for.
When critical portions of your security tech stack rely on time-consuming manual processes, they introduce bottlenecks that drag down security productivity and block growth. At a certain point, establishing secure governance over increasing volumes of data while complying with complex regulations becomes unmanageable.
At the same time, enterprise growth makes it harder for individual security technologies to effectively share critical data with one another in an efficient way.
Again, manual processes will shoulder most of this burden, stretching qualified security expertise thin and making sustainable growth harder to manage.
When the enterprise finds itself targeted by a sophisticated cyberattack, these inefficiencies and production bottlenecks can become critical vulnerabilities. As a result, enterprise leaders are increasingly turning towards security orchestration, automation, and response (SOAR) solutions to close security gaps and automate their most time-consuming security tasks.
Enterprise security teams have larger workloads than ever, and cyberattacks are becoming more frequent every year. The availability of qualified cybersecurity talent remains low across the board, making it difficult for enterprises to effectively meet security challenges.
SOAR solutions allow enterprise security talent to offset some of their most time-consuming tasks while improving security event outcomes. SOAR solutions combine three components to help organizations make the most of their security information and event management (SIEM) solution:
SOAR solutions work by integrating and automating cybersecurity processes throughout the enterprise and triggering comprehensive responses to cyber threats. This makes it easy for organizations to protect themselves from common attacks and known vulnerabilities while immediately prioritizing unknown threats and zero-day exploits.
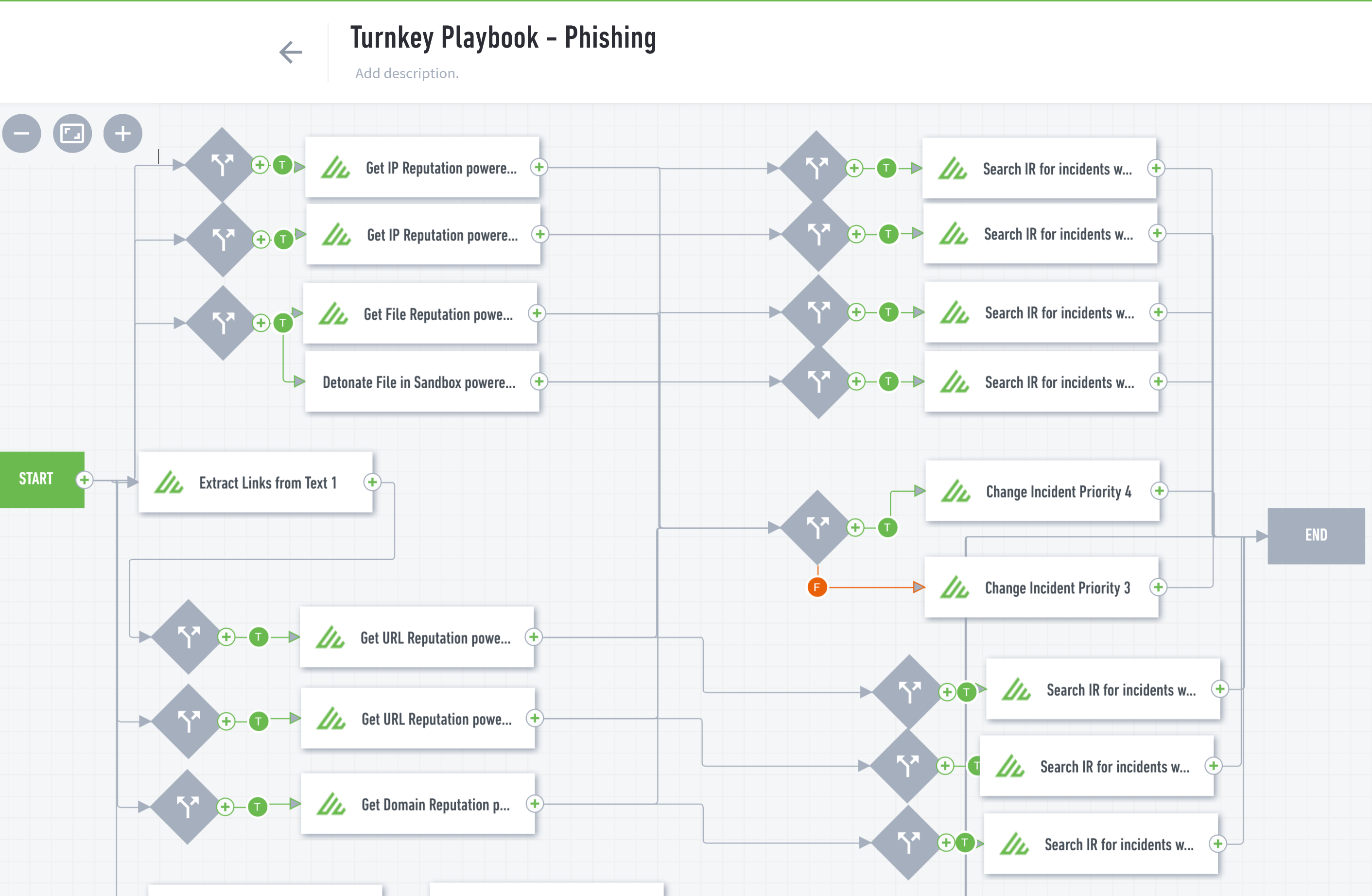
A well-designed SOAR playbook will automatically leverage multiple separate technologies to protect enterprise data and provide human analysts with readymade insight. A simple playbook might look like this:
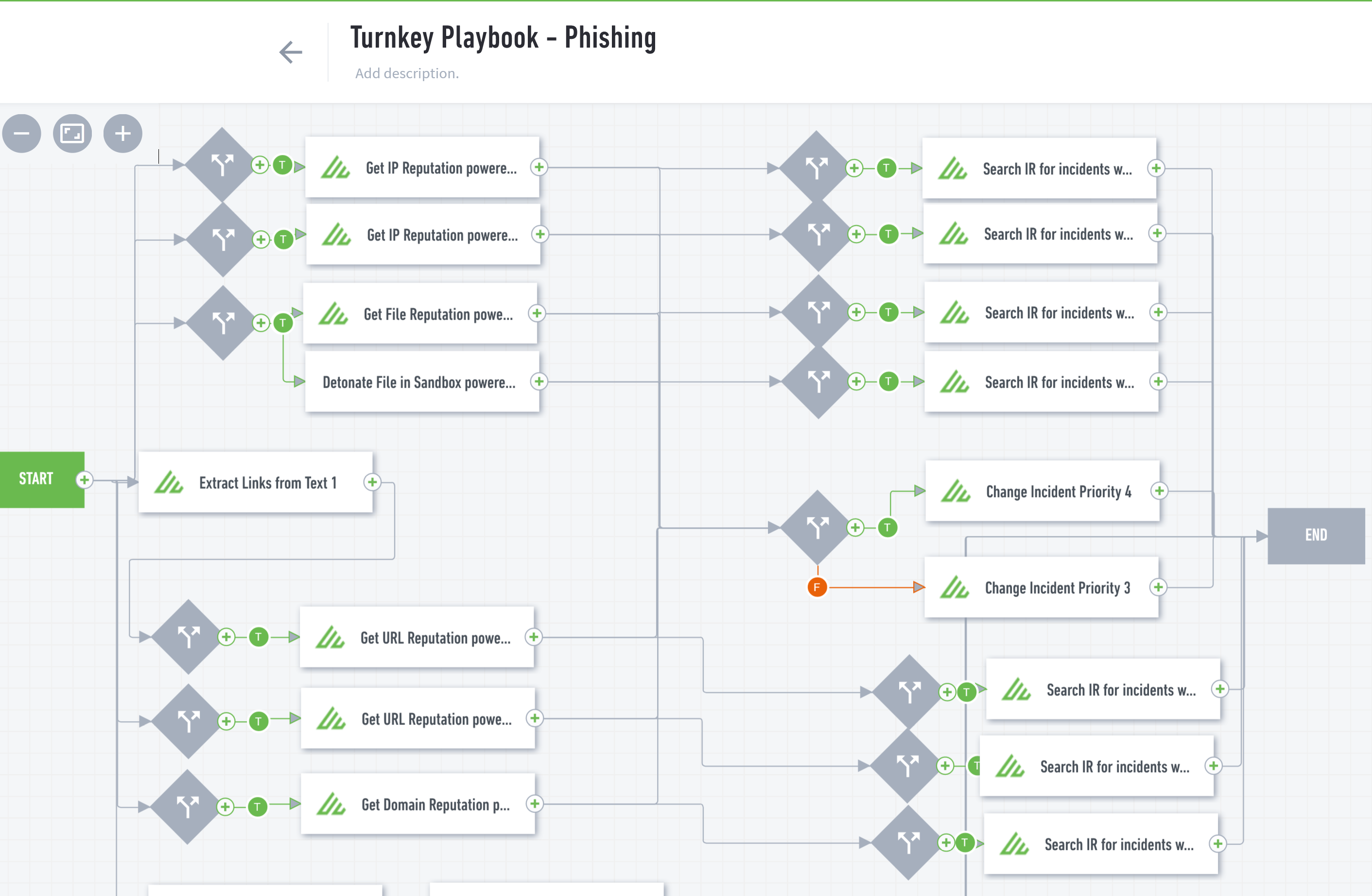
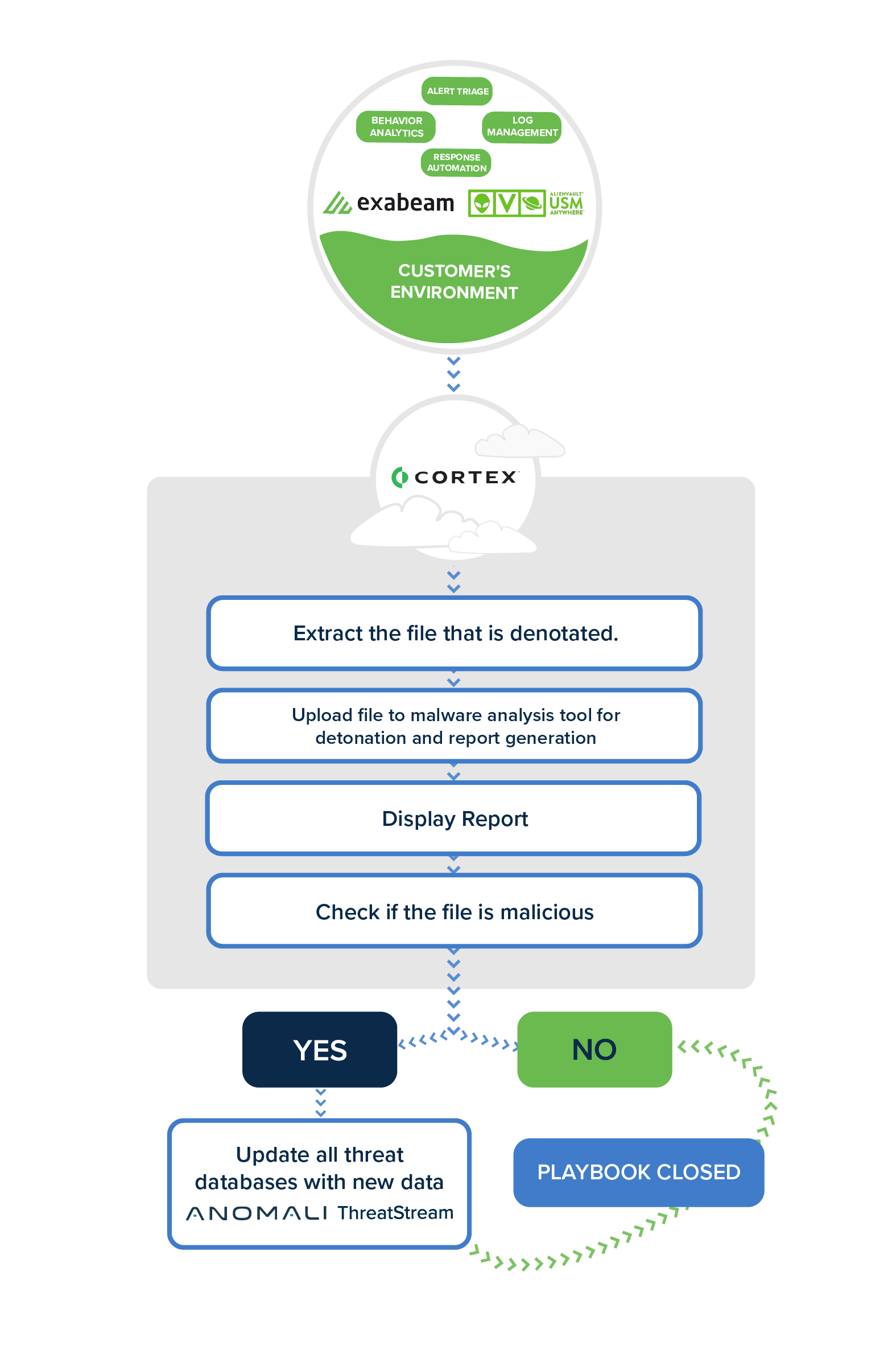
But there is no limit to the logic or complexity that a playbook can follow. Here are just a few examples of SOAR playbooks that an enterprise-level organization might use to reduce friction in its cybersecurity processes and improve security event outcomes:
SOAR platforms play a critical role in helping large organizations scalable go govern cybersecurity operations and improve security investment returns. However, managing a SOAR platform and keeping it up-to-date with the latest attack and threat profiles can be an overwhelming task.
Playbooks are not static documents. They must change to reflect real threats and protect against vulnerabilities in real-time. Effective playbook lifecycle management is a task best-suited to a managed detection and response vendor with comprehensive threat intelligence capabilities.
As your MDR partner, Lumifi can provide valuable expertise and assistance in integrating a comprehensive SOAR platform into your tech stack and providing complete, up-to-date playbooks designed to maximize the effectiveness of your cybersecurity tech stack against today' latest threats.